Checkpoint (JLV) Mac OS
Table of Contents:
- Endpoint Security Clients Downloads
- Utilities/Services Downloads
- Management Console Downloads
- Documentation and Related SecureKnowledge Articles
Mac OS X - Apple Java (prior to Java 1.6.037) Until the release of Mac OS X Lion (10.7.x), Java was included with the operating system. Starting with Mac OS X Lion (10.7.x), Apple does not include Java by default and installation has to be done manually. San Francisco Bay Area College Counselor, Freelance Writer Higher Education Education San Jose State University 2002 — 2004 Bachelor of Arts (B.A.), Sociology University of California, Los Angeles Experience JLV College Counseling March 2014 - Present Examiner.com July 2014 - Present Northwest University June 2010 - November 2012 University.
Endpoint Security Homepage is now available.
Notes:
- The relevant links to downloads are located in the relevant section, i.e. Standalone Clients, Utilities/Services.
- The relevant links to documentation are located in the 'Documentation' section.
- It is strongly recommended that you read the E82.50 Endpoint Security Client for macOS Release Notes and Known Limitations section, before installing this release.
- Also refer to:
- For E82.50 release for Windows: Refer to sk165515 - Enterprise Endpoint Security E82.50 Windows Clients
Endpoint Security Homepage is now available.
Notes:
- The relevant links to downloads are located in the relevant section, i.e., Standalone Clients, Utilities/Services.
- The relevant links to documentation are located in the 'Documentation' section.
- It is strongly recommended that you read the E82.50 Endpoint Security Client for macOS Release Notes
- Also refer to:
What's New in E82.50 for macOS
Show / Hide this sectionIntroduces the Anti-Malware blade for macOS. Currently, it is EA quality, with the blade’s main capabilities, such as:- Displays current status in the client UI.
- Enables full system scan, manual and scheduled by policy.
- Quarantines malicious files and enables the user to restore by policy.
- Updates malware signatures from the Check Point Signature server in the cloud.
- Reports back about malicious files to the Endpoint Management server.
Checkpoint (jlv) Mac Os Catalina
Enhancements
- This release includes stability, quality and performance fixes.
Endpoint Security Clients Downloads
Show / Hide this sectionEndpoint Security E82.50 Clients for macOS
| Platform | Package | Link |
| macOS | E82.50 Check Point Endpoint Security Client for macOS | (ZIP) |
| macOS | E82.50 Check Point Endpoint Security Client for macOS (without Capsule Docs and SandBlast Agent) | (ZIP) |
Standalone Clients Downloads
Show / Hide this sectionNote: These Standalone clients do not require Endpoint Security Server installation as part of their deployment.
E82.50 Standalone Clients for macOS
| Platform | Package | Link |
| macOS | E82.50 Endpoint Security VPN for macOS - Disc Image (DMG) | (DMG) |
| E82.50 Endpoint Security VPN for macOS - Automatic Upgrade package (PKG) | (PKG) | |
| E82.50 Endpoint Security VPN for macOS - Signature for automatic upgrade | (signature) |
Capsule Docs E82.50 Clients
| Platform | Package | Link |
| macOS | E82.50 Capsule Docs Mac Editor |
Utilities/Services Downloads
Show / Hide this sectionMedia Encryption Offline Access Tool E82.xx for macOS
| Platform | Package | Link |
| macOS | E82.xx Media Encryption Offline Access Tool |
Native Encryption Management Hotfix Downloads
Show / Hide this sectionIf you want to use the new Native Encryption Management, download the relevant hotfix.Note: In order to download some of the packages you will need to have a Software Subscription or Active Support plan.
The packages provided below are Legacy CLI packages (not CPUSE packages).
| Endpoint Security Server | Package | Link |
| R77.30.03 | R77.30.03 Server Hotfix for Native Encryption Management | (TGZ) |
| R77.20 EP6.2 | R77.20 EP6.2 Server Hotfix for Native Encryption Management | (TGZ) |
Important: The Native Encryption Management Hotfix is integrated into R80.20
Management Console Downloads
Show / Hide this sectionManagement Console for Endpoint Security Server
The SmartConsole for Endpoint Security Server allows the Administrator to connect to the Endpoint Security Server and to manage the new Endpoint Security Software Blades.
| Endpoint Security Server | Package | Link |
| R77.30.03 | SmartConsole for Endpoint Security Server R77.30.03 / E80.89 | (EXE) |
| R77.20 EP6.2 | SmartConsole for Endpoint Security Server R77.20 EP6.2 / E80.89 | (EXE) |
| R80.20 | SmartConsole for Endpoint Security Server R80.20 | sk137593 |
| R80.30 | SmartConsole for Endpoint Security Server R80.30 | sk153153 |
| R80.40 | SmartConsole for Endpoint Security Server R80.40 | sk165473 |
Known Limitations
Show / Hide this section| Issue ID | Description |
| EPS-23363 | On macOS 10.15 Catalina, Full Disk Access has to be approved for several blades to work properly, including Media Encryption, VPN, Threat Emulation, Anti-Ransomware and Forensics. macOS does not provide any notifications about this automatically, so Endpoint Security presents a UserCheck message, as a guide for which application to grant FDA access, and a button to open the System Preferences. |
| AHTP-15580 | Post-upgrade from the E80.89 release, there are no historic AR/TE events shown in the UI. |
| AHTP-15310 | If nodeJS is installed on the Mac, build directories should be excluded in SBA policy (AR/EFR and TE) to improve performance. |
| EPS-23361 | If the default name of the compliance rule for checking if assigned blades are running is changed, i.e. cloned or edited, this rule will not be applied to the macOS compliance blade. Then, on the server side there will be no compliance reporting (inform, warn, restrict). Client will also not go into the assumed compliance state. |
| ESVPN-1920 | In some rare cases during the upgrade of VPN client from previous version, user may experience temporary inability to connect to VPN site. Delay may be from seconds to several minutes. To address this issue user should perform reboot of operating system. |
| EPS-26022 | Media Encryption blade: Media scan - not supported. |
Anti-Malware Blade Limitations
| Issue ID | Description |
| EPS-26010 | Enable Web protection - not supported (always off) |
| EPS-26011 | Scan Mail messages - not supported (always off) |
| EPS-26012 | Signature source settings - not supported (only External Check Point Signature server setting is supported) |
| EPS- 26014 | Push operations:
|
| EPS-26015 | Scan targets settings:
|
| EPS-26016 | Configure threat cloud knowledge sharing - not supported |
| EPS-26017 | Process exclusion - MD5 not supported |
| EPS-26020 | Contextual scan - not supported (Finder does not have option for scan) |
| EPS-26059 | Anti-Malware detections integration with Forensics report - not supported. |
Documentation and Related SecureKnowledge Articles
Show / Hide this section| Document |
| E82.50 Endpoint Security Client for Mac |
| E82.50 Endpoint Security Client for macOS Release Notes |
| Remote Access VPN Clients |
| E82.50 Endpoint Security VPN Clients for macOS Release Notes |
| E80.71 and higher Endpoint Security VPN for Mac Administration Guide |
For more information on Check Point releases see: Maintrain Release map, Maintrain Upgrade map, Maintrain Backward Compatibility map, Maintrain Releases plan.
For more information on the Enterprise Endpoint Security E82.00 Client, see:
You can also visit our Endpoint forum, Remote Access forum, Capsule Docs forum, or any other CHECKMATES forum to ask questions and get answers from technical peers and Support experts.For more information on Check Point releases see: Maintrain Release map, Maintrain Upgrade map, Maintrain Backward Compatibility map, Maintrain Releases plan.
For more information on the Enterprise Endpoint Security E80.71 Client, see:
- For installation and upgrade instructions, use the procedures in: Installation and Upgrade Guide for Gaia Platforms R77 Versions
Revision History
Show / Hide this section| Date | Description |
| 07 Apr 2020 | First release of this document. |
In This Section: |
Providing Secure Remote Access
In today's business environment, it is clear that workers require remote access to sensitive information from a variety of locations and a variety of devices. Organizations must also make sure that their corporate network remains safe and that remote access does not become a weak point in their IT security.
This chapter:
- Gives you information about Check Point's secure remote access options.
- Helps you decide which remote access client or clients best match your organization's requirements.
- Shows you where to get more information.
Types of Solutions
All of Check Point's Remote Access solutions provide:
- Enterprise-grade, secure connectivity to corporate resources.
- Strong user authentication.
- Granular access control.
Factors to consider when choosing remote access solutions for your organization:
- Client-Based vs. Clientless - Does the solution require a Check Point client to be installed on the endpoint computer or is it clientless, for which only a web browser is required. You might need multiple solutions within your organization to meet different needs.
- Secure Connectivity and Endpoint Security - Which capabilities does the solution include?
- Secure Connectivity - Traffic is encrypted between the client and VPN gateway. After users authenticate, they can access the corporate resources that are permitted to them in the access policy. All Check Point solutions supply this.
- Endpoint Security - Endpoint computers are protected at all times, even when there is no connectivity to the corporate network. Some Check Point solutions supply this.
Client-Based vs. Clientless
Check Point remote access solutions use IPsec and SSL encryption protocols to create secure connections. All Check Point clients can work through NAT devices, hotspots, and proxies in situations with complex topologies, such as airports or hotels. These are the types of installations for remote access solutions:
- Client-based - Client application installed on endpoint computers and devices. Clients are usually installed on a managed device, such as a company-owned computer. The client supplies access to most types of corporate resources according to the access privileges of the user.
- Clientless - Users connect through a web browser and use HTTPS connections. Clientless solutions usually supply access to web-based corporate resources.
- On demand client - Users connect through a web browser and a client is installed when necessary. The client supplies access to most types of corporate resources according to the access privileges of the user.
Secure Connectivity and Endpoint Security
You can combine secure connectivity with additional features to protect the network or endpoint computers.
- Secure Connectivity - Traffic is encrypted between the client and VPN gateway and strong user authentication is supported. All Check Point solutions supply this.
These solutions require licenses based on the number of users connected at the same time.
- Security Verification for Endpoint computers - Makes sure that devices connecting to the gateway meet security requirements. Endpoint machines that are not compliant with the security policy have limited or no connectivity to corporate resources. Some Check Point solutions supply this.
- Endpoint Security:
- Desktop Firewall - Protects endpoint computers at all times with a centrally managed security policy. This is important because remote clients are not in the protected network and traffic to clients is only inspected if you have a Desktop Firewall. Some Check Point solutions supply this
- More Endpoint Security Capabilities - Check Point solutions can include more Endpoint Security capabilities, such as anti-malware, disk encryption and more.
These solutions require licenses based on the number of clients installed.
Remote Access Solution Comparison
Details of the newest version for each client and a link for more information are in sk67820.
SSL VPN Portal and Clients
Name | Supported Operating Systems | Client or Clientless | Encryption Pr otocol | Security Verification for Endpoint Devices | Desktop Firewall on Endpoint Devices | IPv6 Support |
|---|---|---|---|---|---|---|
Mobile Access Web Portal | Windows, Linux, Mac OS, iOS, Android | Clientless | SSL | R77.10 and higher | ||
SSL Network Extender for Mobile Access Blade | Windows, Linux, Mac OS | On-demand Client through Mobile Access Portal) | SSL | |||
Capsule Workspace for iOS (previously Mobile Enterprise) | iOS | Client | SSL | Jailbreak & Root Detection MDM Cooperative Enforcement (sk98201) | R77.10 and higher | |
Capsule Workspace for Android (previously Mobile Enterprise) | Android | Client | SSL | Jailbreak & Root Detection MDM Cooperative Enforcement (sk98201) | R77.10 and higher |
Layer-3 VPN Tunnel Clients
Name | Supported Operating Systems | Client or Clientless | Encryption Protocol | Security Verification for Endpoint Devices | Desktop Firewall on Endpoint Devices | IPv6 Support |
|---|---|---|---|---|---|---|
Capsule Connect for iOS (previously Mobile VPN) | iOS | Client | IPsec / SSL | MDM Cooperative Enforcement (sk98201) | ||
Capsule VPN for Android (previously Mobile VPN) | Android | Client | IPsec/SSL | MDM Cooperative Enforcement (sk98201) | ||
Check Point VPN Plugin for Windows 8.1 | Windows 8.1 | Pre- installed client | SSL | |||
Check Point Mobile for Windows | Windows | Client | IPsec |
Layer-3 VPN Tunnel Clients Integrated with Endpoint Security
Name | Supported Operating Systems | Client or Clientless | Encryption Protocol | Security Verification for Endpoint Devices | Desktop Firewall on Endpoint Devices | IPv6 Support |
|---|---|---|---|---|---|---|
Endpoint Security VPN for Windows | Windows | Client | IPsec | |||
Endpoint Security VPN for Mac | Mac OS | Client | IPsec | |||
Endpoint Security Suite Remote Access VPN Blade | Windows, Mac OS | Client | IPsec |
Additional Remote Access Solutions
Name | Supported Operating Systems | Client or Clientless | Encryption Protocol | Security Verification for Endpoint Devices | Desktop Firewall on Endpoint Devices | IPv6 Support |
|---|---|---|---|---|---|---|
SecuRemote | Windows | Client | IPsec | |||
Check Point GO VPN | Windows | Clientless - Requires a Check Point GO device | SSL |
Summary of Remote Access Options
Below is a summary of each Remote Access option that Check Point offers. All supply secure remote access to corporate resources, but each has different features and meets different organizational requirements.
Details of the newest version for each client and a link for more information are in sk67820.
Mobile Access Web Portal
The Mobile Access Portal is a clientless SSL VPN solution. It is recommended for users who require access to corporate resources from home, an internet kiosk, or another unmanaged computer. The Mobile Access Portal can also be used with managed devices.
It provides:
- Secure Connectivity
- Security Verification
The Mobile Access Portal supplies access to web-based corporate resources. You can use the on-demand client, SSL Network Extender, through the Portal to access all types of corporate resources.
Required Licenses: Mobile Access Software Blade on the gateway.
Supported Platforms: Windows, Mac OS X, Linux, iOS, Android
Where to Get the Client: Included with the Security Gateway. See sk67820.
SSL Network Extender
SSL Network Extender is a thin SSL VPN on-demand client installed automatically on the user's machine through a web browser. It supplies access to all types of corporate resources.
SSL Network Extender has two modes:
- Network Mode - Users can access all application types (Native-IP-based and Web-based) in the internal network. To install the Network Mode client, users must have administrator privileges on the client computer.
Supported Platforms: Windows, Mac OS X, Linux
- Application Mode - Users can access most application types (Native-IP-based and Web-based) in the internal network, including most TCP applications. The user does not require administrator privileges on the endpoint machine.
Supported Platforms: Windows
Required Licenses:
Mobile Access Software Blade on the gateway
Where to Get the Client: Included with the Security Gateway. See sk67820.
Capsule Workspace for iOS
Capsule Workspace for iOS is an SSL VPN client. It supplies secure connectivity and access to web-based corporate resources and Microsoft Exchange services. It also gives secure access to Capsule Docs protected documents It was previously called Mobile Enterprise.
Capsule Workspace is ideal for mobile workers who have privately-owned smart phones or tablets. It protects only the business data inside the App and does not require device-level security measures, such as device-lock or device-wipe.
Required Licenses: Mobile Access Software Blade on the gateway
Supported Platforms: iOS
Where to Get the Client: Apple App Store
Capsule Workspace for Android
Capsule Workspace for Android is an SSL VPN client. It supplies secure connectivity and access to web-based corporate resources and Microsoft Exchange services. It also gives secure access to Capsule Docs protected documents It was previously called Mobile Enterprise.
Capsule Workspace for Android is ideal for mobile workers who have privately-owned smart phones or tablets. It protects only the business data inside the App and does not require device-level security measures, such as device-lock or device-wipe.
Required Licenses: Mobile Access Software Blade on the gateway
Supported Platforms: Android
Where to Get the Client: Google Play Store
Capsule Connect for iOS
Capsule Connect is a full L3 tunnel app that gives users network access to all mobile applications. It supplies secure connectivity and access to all types of corporate resources. It was previously called Mobile VPN.
Required Licenses: Mobile Access Software Blade on the gateway
Supported Platforms: iOS 6.0 +
Where to Get the Client: Apple App Store
Capsule VPN for Android
Capsule VPN for Android devices is an L3 VPN client. It supplies secure connectivity and access to corporate resources using L3 IPSec/SSL VPN Tunnel. It was previously called Mobile VPN.
Required Licenses: Mobile Access Software Blade on the gateway
Supported Platforms: Android 4 + (ICS+)
Where to Get the Client: Google Play Store
Check Point VPN Plugin for Windows 8.1
Check Point VPN Plugin for Windows 8.1 is an L3 VPN client. It supplies secure connectivity and access to corporate resources using L3 SSL VPN Tunnel.
Required Licenses: Mobile Access Software Blade on the gateway
Supported Platforms: Windows 8.1
Where to Get the Client: Pre-installed with Windows.
Check Point Mobile for Windows
Check Point Mobile for Windows is an IPsec VPN client. It is best for medium to large enterprises that do not require an Endpoint Security policy.
It provides:
- Secure Connectivity
- Security Verification
Required Licenses: IPsec VPN and Mobile Access Software Blades on the gateway.
Supported Platforms: Windows
Where to Get the Client: Check Point Support Center - sk67820.
Endpoint Security VPN
Endpoint Security VPN is an IPsec VPN client that replaces SecureClient. It is best for medium to large enterprises.
It provides:
- Secure Connectivity
- Security Verification
- Endpoint Security that includes an integrated Desktop Firewall, centrally managed from the Security Management Server.
Required Licenses: The IPsec VPN Software Blade on the gateway, an Endpoint Container license, and an Endpoint VPN Software Blade license on the Security Management Server.
Supported Platforms: Windows
Where to Get the Client: Check Point Support Center - sk67820.
Note - Endpoint Security VPN on Mac OS X includes a Desktop Firewall but not Security Verification. |
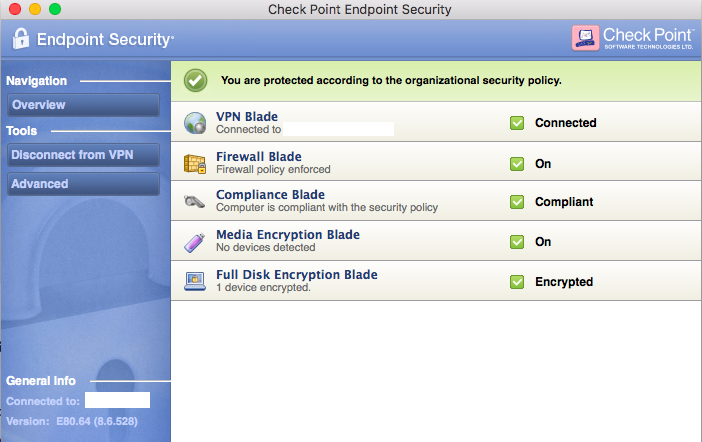
Endpoint Security VPN for Mac
Endpoint Security VPN combines Remote Access VPN with Endpoint Security in a client that is installed on endpoint computers. It is recommended for managed endpoints that require a simple and transparent remote access experience together with desktop firewall rules. It includes:
- Enterprise Grade Remote Access Client that replaces SecureClient for Mac.
- Integrated Desktop Firewall, centrally managed from the Security Management Server.
Required Licenses: The IPsec VPN Software Blade on the gateway, an Endpoint Container license, and an Endpoint VPN Software Blade license on the Security Management Server.
Supported Platforms for Users: Mac OS X
Where to Get the Client: Check Point Support Center - sk67820.
Endpoint Security Suite
The Endpoint Security Suite simplifies endpoint security management by unifying all endpoint security capabilities in a single console. Optional Endpoint Security Software Blades include: Firewall, Compliance Full Disk Encryption, Media Encryption & Port Protection, and Anti- Malware & Program Control. As part of this solution, the Remote Access VPN Software Blade provides full, secure IPsec VPN connectivity.
The Endpoint Security suite is best for medium to large enterprises that want to manage the endpoint security of all of their endpoint computers in one unified console.
Required Licenses: Endpoint Security Container and Management licenses and an Endpoint VPN Software Blade on the Security Management Server.
Supported Platforms: Windows, Mac OS X
Where to Get the Client: Check Point Support Center - sk67820.
SecuRemote
SecuRemote is a secure, but limited-function IPsec VPN client. It provides secure connectivity.
Mac Os Download
Required Licenses: IPsec VPN Software Blade on the gateway. It is a free client and does not require additional licenses.
Checkpoint (jlv) Mac Os Update
Supported Platforms: Windows
Where to Get the Client: Check Point Support Center - sk67820.
Check Point GO
Check Point GO is a portable workspace with virtualized Windows applications, on a secure and encrypted USB Flash Drive. Users insert the USB device into a host PC and securely access their workspace and corporate resources through SSL VPN technology.
Check Point GO is ideal for mobile workers, contractors, and disaster recovery. The virtual workspace is segregated from the host PC and controls the applications and data that can run in Check Point GO.
It provides:
- Secure Connectivity
- Security Verification
Required Licenses: IPsec VPN Software Blade on the gateway and Check Point GO devices.
Mac Os Mojave
Supported Platforms: Windows
Where to Get the Client: Check Point Support Center - sk67820.